SEQRITE ENDPOINT SECURITY
Seqrite Endpoint Security (EPS) is a comprehensive cybersecurity solution designed to detect, prevent, and respond to advanced cyber threats targeting enterprise devices. With over 25 years of innovation in cybersecurity, Seqrite protects organizations against malware, ransomware, zero-day attacks, and data breaches, while offering centralized control over all connected endpoints.
Seqrite Endpoint Security is a holistic solution to detect, prevent, and respond to advanced cyber threats targeting enterprise endpoints.
It provides a centralized management and protection of network-connected devices (endpoints) such as laptops, desktops, mobile devices, and servers from cyber threats. It uses policies, and techniques to prevent unauthorized access, malware infections, and data breaches, ensuring these entry points to a corporate network or cloud services are secured.
Key components include Endpoint Protection Platforms (EPPs) for anti-malware, and Endpoint Detection and Response (EDR) for more advanced threat detection and analysis.
WHY CHOOSE SEQRITE ENDPOINT SECURITY
Complete Enterprise Protection
Proven cybersecurity provider with 7.1 million active licenses across 80+ countries.
25+ years of research and development in enterprise security.
Trusted by organizations to safeguard sensitive data and IT infrastructure.
In today’s rapidly evolving cyber threat landscape, enterprises need more than just traditional antivirus. Seqrite Endpoint Security provides a holistic, AI-driven defense solution that protects endpoints, secures data, and ensures business continuity. Whether on-premise or cloud-based, Seqrite EPS is the intelligent choice for organizations seeking reliable endpoint protection.
WHY SEQRITE ENDPOINT SECURITY MATTERS
Your devices are entry points for cyber-criminals
Endpoints such as laptops, desktops, mobile devices, servers, IoT systems, and POS terminals are common entry points for cybercriminals. As remote work, cloud adoption, and mobile apps increase, the attack surface has expanded, making endpoint security a critical defense strategy.
The Security engine is designed to be Lightweight and highly efficient, providing robust protection without consuming significant system resources like CPU or RAM.
Without proper endpoint protection, enterprises risk:
- Unauthorized access and data breaches
- Ransomware and fileless malware infections
- Data loss through compromised devices
- Non-compliance with industry regulations
Sophisticated threats:
Cybercriminals are constantly evolving their methods, leading to advanced attacks like ransomware and fileless malware that can bypass traditional security measures.
Data loss prevention:
Endpoint security helps prevent malicious actors from exfiltrating sensitive data from compromised devices.
Key Benefits:
- Protects endpoints or devices from all types of malware, ransomware, and zero-day exploits.
- Enhances the overall enterprise security.
- Improves visibility with centralized monitoring and control
- Helps organizations meet industry compliance requirements.
- Provides greater visibility into security events.
- Reduces IT costs by preventing costly breaches. Security breaches can cost organizations millions of dollars.

FEATURES OF SEQRITE ENDPOINT SECURITY
with Go Deep AI-powered threat-hunting engine
Scalability and Cross-Platform Support:
✓ Enjoy seamless scalability and robust security across Windows, Mac, and Linux platforms, meeting diverse organizational needs
Zero day attack defense:
✓ Detects the “DNA” of Malwares
✓ Zero-day attack defense (Detects new & unknown threats)
✓ Blocks threats by analyzing behavioral patterns
✓ Goes beyond traditional signature-based antivirus systems
Cloud-Based Management:
✓ Access the security dashboard from the cloud to enforce policies on the go and ensure compliance across all endpoints.
Web & Email Security:
✓ Email protection
✓ Browsing protection
✓ Web filtering
Data & Disk Security:
✓ BitLocker disk encryption
✓ Data Loss Prevention (DLP)
✓ File hash scans & real-time blocking
✓ File activity monitoring & sandboxing
Deployment Flexibility:
✓ Available in both On-premise and Cloud editions, giving enterprises the flexibility to choose based on their IT strategy.
Threat Detection & Response:
✓ Endpoint Threat Hunting (ETH)
✓ Endpoint Detection & Response (EDR)
✓ Anti-ransomware protection
✓ Firewall / IDS / IPS protection
✓ Phishing protection
✓ Vulnerability scans
Management & Monitoring:
✓ Asset management
✓ Multi-site management
✓ Patch management
✓ Email & SMS notifications
✓ System tune-up
✓ Central dashboard for easy device management
Device & Access Control:
✓ Remote roaming device management
✓ Enterprise mobile device management
✓ Central dashboard for device policy enforcement
✓ Automatic OS Patch Management
✓ Enhanced device control
✓ Application control
WHAT IS SEQRITE EPS GO DEEP AI
Seqrite Endpoint Security (EPS) uses a next-generation threat-hunting engine called Go Deep AI to provide advanced protection against cyber threats. Unlike traditional antivirus software that relies on known malware signatures, Go Deep AI proactively analyzes the fundamental characteristics of threats to eliminate them before they can cause harm.
Go Deep AI works by:
Analyzing Malware DNA:
It studies the structural and behavioral patterns of malware, how it spreads, behaves, and interacts with a system to understand its “genetic makeup.”
Proactive Zero-Day Defense:
This unique approach allows it to detect and eliminate new, sophisticated, and unknown threats (zero-day attacks) that can easily bypass signature-based detection.
By focusing on the behavior of malware, Seqrite’s Go Deep AI provides a powerful and proactive defense that is effective against the constantly evolving threat landscape.

SEQRITE MOBILE DEVICE MANAGEMENT (MDM)
Seqrite’s Mobile Device Management (MDM) is a security-first solution designed to streamline the management of mobile devices for businesses. As an Android Enterprise Silver Partner, it provides a unified web console for comprehensive protection and management of company owned devices.
The solution enhances productivity by offering seamless management, app distribution, and control.
Key features include:
AI-Driven Security:
Uses the GoDeep.AI engine for built-in antivirus and web protection to guard against phishing and other threats.
Granular Policy Control:
Allows administrators to set up geo-, Wi-Fi-, and time-based restrictions to enforce security policies.
Remote Management:
Provides the ability to remotely manage data on Android and iOS devices, including remote wipe and reset capabilities to ensure data security.
Simplified App Management:
Supports kiosk mode and custom app deployment to ensure employees only use approved applications for work.
Real-time Monitoring:
Offers an interactive dashboard with visual reports and comprehensive activity logs for auditing and monitoring device usage.
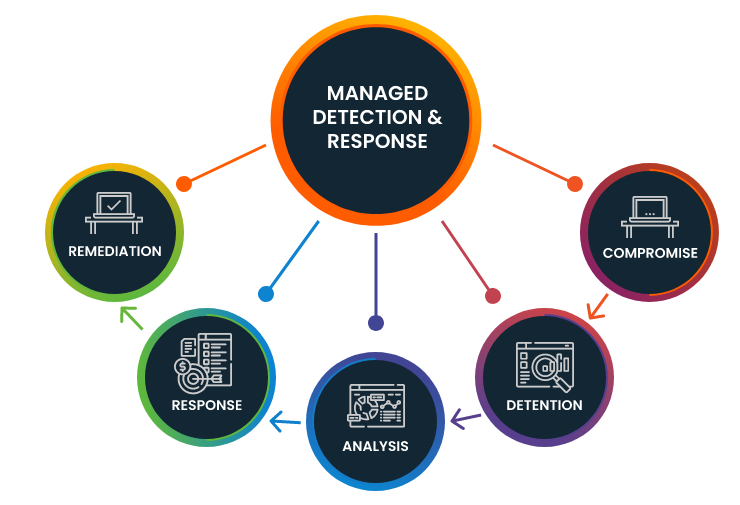
Seqrite EDR vs XDR: The Evolution of Cybersecurity
At Seqrite, we see Extended Detection and Response (XDR) as the next step in the evolution of cybersecurity solutions, moving beyond the traditional Endpoint Detection and Response (EDR) approach.
Endpoint Detection and Response (EDR):
Our EDR solutions provide a security-first approach focused on securing individual endpoints. They are highly effective at detecting, analyzing, and responding to threats that originate from or target your devices.
Extended Detection and Response (XDR):
Our XDR platform takes this protection to the next level. It unifies threat data from all your security layers—endpoints, email, servers, and cloud workloads. By leveraging advanced analytics and machine learning, Seqrite XDR provides a unified view of your entire security landscape. This allows our solution to:
Enhance Visibility:
Give you a comprehensive, single-pane-of-glass view of all threats.
Improve Alert Management:
Prioritize critical incidents to help your security team focus on what matters most.
Increase Efficiency:
Automate threat detection, analysis, and response across your entire digital environment.
Seqrite XDR empowers security teams to gain a deeper understanding of complex cyber incidents and respond faster than ever before.

