CYBERSECURITY
In today’s world of evolving threats, Cybersecurity is very critical to every organization because it protects your devices, secures your data, applications and network. Cybersecurity helps to prevent unauthorized access to your data, applications, network, devices and endpoints.
Computer networks transmit data to and fro and hence requires 100% network security. It is not enough to just deploy a firewall solution and go to sleep.
Nowadays Hackers can launch brute force login, harvest passwords from the network and even perform hands on keyboard live attack. A Hands-On-Keyboard attack is when a threat actor is manually and actively trying to exploit a host rather than using scripted commands to bypass security solutions.
You need an automated Endpoint detection and response (EDR) solution and maybe our Cybersecurity as a service solution also.
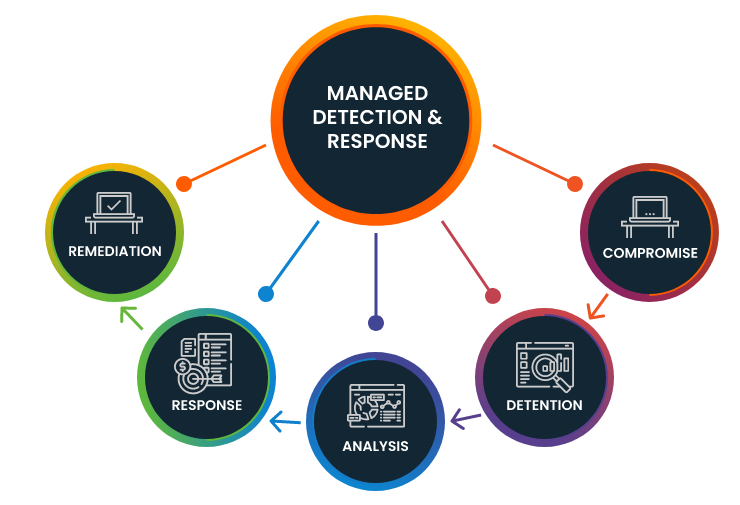
Netcat provides security as a service through our expert-led managed threat hunting. This is called Managed Detection & Response (MDR) to secure your data, applications, endpoints and network from any form of attack.
CYBERSECURITY TOOLS
Sophos provides seamless integration with a wide range of cybersecurity solutions.Looking for Sophos Managed Detection and Response (MDR)?









UNIFIED THREAT MANAGEMENT FIREWALL APPLIANCES
These information security devices serve as an all-in-one security tool. Unified Threat Management appliances includes firewalls that features: content filtering, web caching, intrusion prevention system, DoS attack prevention, application filtering, gateway anti-virus, spam anti-virus, captive portal, bandwidth management, Network Access Control, blocking of malicious Web sites, screening of e-mail for spam and etc.
They combine most of these features to provide network, data, and application security. websites can be blocked based on categories like pornography, drugs, Alcohol, weapons, violence and more.
A firewall secures the network traffic. A firewall establishes a barrier between a trusted internal network and the external networks such as the internet.
Every data entering or leaving the network goes through the firewall to be examined for security threats. A firewall makes it harder for hackers to attack your network.
Netcat have partnered with Sophos, Fortinet, Seqrite and Cisco to enable us protect your enterprise from malicious attacks.

SOPHOS ENDPOINT DETECTION & RESPONSE (EDR) WITH EXPERT-LED THREAT HUNTING
Endpoint detection and response (EDR) is a cybersecurity solution that captures all endpoint activity and advanced analytics to provide real-time visibility into the health of all endpoints, detect malicious activity, alert the information security team and provide remediation suggestions and capabilities to respond, stop an attack in progress or limit its spread.
As cyber threats continue to evolve and become more sophisticated, organizations must constantly improve their security posture to stay ahead of potential attacks. One effective way to do this is through threat hunting, a proactive approach to identifying and mitigating potential security threats before they can cause damage. However, threat hunting can be a time-consuming and resource-intensive process, which is where extended detection and response (XDR) comes in.
When combined with threat hunting, XDR can significantly enhance an organization’s security posture.

FEATURES OF ENDPOINT DETECTION & RESPONSE (EDR)
Endpoint monitoring
Data search, investigation and threat hunting
Alert triage or suspicious activity validation
Suspicious activity detection
Data analysis
Event Recording
Actionable intelligence to support response
Remediation
SOPHOS MANAGED DETECTION & RESPONSE (MDR) - CYBERSECURITY AS A SERVICE
Netcat provides cybersecurity as a service through our expert-led managed threat hunting. This service provides round-the-clock monitoring of your servers and devices to discover attacks anywhere in your organization. Our threat hunters work on your behalf to discover advanced threats, such as state-sponsored attackers, cybercriminals, malicious insiders and malwares.
Our Managed detection and response (MDR) endpoint security as a services typically includes:
Continuous monitoring
Threat hunting
Prioritization of threats and alerts
Managed investigation services
Guided response
Managed remediation
The major advantage of MDR, cybersecurity as a service is that it quickly helps to identify and mitigate the impact of threats without the need for additional staffing. There is a global shortage of highly skilled cybersecurity professionals.
SOPHOS EXTENDED DETECTION AND RESPONSE (XDR)
EDR solutions only monitor a single layer of the endpoints security architecture at a time.
While XDR solution can collect data from multiple endpoints, servers, firewalls, switches, and other security devices spread across your network and centralizes that intelligence analytics in a single dashboard or console.
XDR solution monitors all of your endpoints as well as your entire environment to give you greater visibility. Defend against endpoint, user, and network attacks. XDR is fully automated to mitigate any potential attack before it becomes a threat.
Relying on multiple individual security tools often create silos and gaps within the security architecture. The more complicated the security silos, the greater the likelihood that a security gap will be created and go unnoticed until there’s a breach.
XDR solves this problem by using a unified approach to detecting threats and responding to them. It automatically collects detections and data analytics from all the different security layers, producing a superset of information that, when correlated, helps hasten and enhance threat detection. This enables security analysts to investigate incidents quickly and to take action immediately.
Extended Detection and Response (XDR) Overview:
Do it yourself threat hunting and detection
Built on the world’s best endpoint protection
Add expertise, not headcount with intelligent XDR
First XDR build for security analysts and IT admins
Holistic telemetry that spans the entire IT environment.
24 x 7 coverage of the organisation’s full IT ecosystem
Actionable cyber threat intelligence
Reduced cost of ownership.
More efficient prioritisation of cybersecurity alerts.
Advanced threat identification and remediation.
Automatic cybersecurity framework mapping.
Sophos XDR is the only tool that enables you to work with your current cybersecurity tools and helps keep your cybersecurity operations simple and effective. Instead of complicating your cybersecurity operations with multiple tools.
Say no to multilayered defense strategy. Sophos XDR coordinates and extends the value of siloed security tools, unifying and streamlining security analysis, investigation and remediation into one consolidated console. As a result, XDR dramatically improves threat visibility, accelerates security operations, reduces total cost of ownership (TCO) and eases the ever-present security staffing burden.
SOPHOS XDR-READY SOLUTIONS INTEGRATED INTO SOPHOS XDR PLATFORM
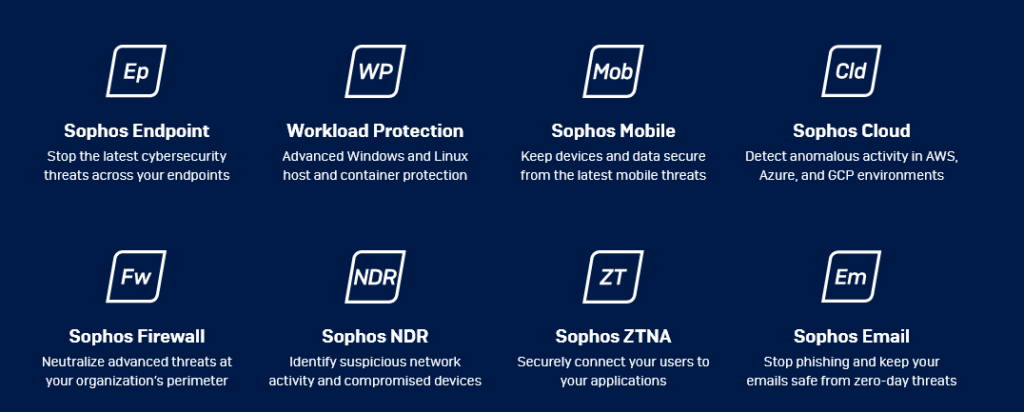
More companies trust Sophos XDR than any other cybersecurity tools.
Instant Security Operations Center
Achieve superior cybersecurity outcomes through a fully-managed MDR service or self-managed security operations platform. Stop being overwhelmed by alerts and start uplevelling your resources to focus on the most strategic issues for your business.
Compatible With What You Already Have
Get more value from your existing investments with security that integrates with your IT stack. Our ever-expanding list of 3rd party integrations includes SOAR, SIEM, ITSM, threat intel, and RMM/PSA tools with plans to support many more.
Non-stop Threat Detection and Response
Proactive threat hunting, investigation, and incident response through our managed detection and response (MDR) services. Delivered by an elite team of experienced threat hunters to support organizations of all sizes.
More than 20,000 customers use Sophos Managed Detection and Response
With 3x more MDR customers than any other cybersecurity vendor, Sophos has the experience to deliver the best possible cybersecurity outcomes. Our expert threat hunters and incident response team monitor your systems on your behalf to detect and eliminate advanced threats. Sophos Managed Detection and Response is the future of cybersecurity.

SEQRITE ENDPOINT SECURITY(EPS)
cutting-edge protection for your network and connected devices
As threats keeps evolving, Seqrite endpoint security suite offers cutting-edge protection for your network and connected devices. From detection scans to asset management, Seqrite Endpoint Security ensure complete network and data protection to address cyber threats.
Seqrite Endpoint Security has advanced features like Behavioural Detection System, Advanced DNA Scan, Endpoint Threat Hunting, Data Loss Prevention, Real-Time Notification, and many more to ensure multi-layered protection for connected devices.
The Centralised Dashboard helps you to keep a tab on your network and connected devices too.


SEQRITE HAWKKPROTECT
Secure user's access to enterprise applications from anywhere
VPN encrypts your internet connection, enhancing the security and privacy of online activities. Your original IP address is hidden, and your data is encrypted, rendering it unreadable to anyone who might intercept it. VPN can protect you from Man-in-the-Middle (MiTM) attacks especially when you use public Wifi.
But VPN is not foolproof. VPN can only guard against specific types of attacks. They aren’t a panacea for all cyber threats. Here are a few limitations:
- Phishing attacks
- Malware
- Many VPN services don’t have AES-256 security Protocols
- Data Leakage protection. Many VPN services don’t have a kill switch that automatically disconnects the user from the internet if the VPN connection fails
SEQRITE HawkkProtect secures your enterprise applications by enforcing a zero-trust user access policy. HawkkProtect secure and centralized platform eliminates the need for VPNs while providing complete visibility on all user activity, ensuring maximum protection for your enterprise applications and services.
With zero-trust user access policy enforcement, HawkkProtect ensures user access is verified, and only the required level of access is provided every single time.

